

For one it’s just technicalities for another it’s the distinction between a company going out of their way to block repairs or a company just not caring and mainly focussing on their own repair process.
Indie iOS app developer with a passion for SwiftUI


For one it’s just technicalities for another it’s the distinction between a company going out of their way to block repairs or a company just not caring and mainly focussing on their own repair process.


There are a couple of concerns with biometrics.
The big one is, as you already mentioned, spoofing biometrics.
The FaceID or TouchID sensor essentially saying “I got that face/fingerprint that you have in your Secure Enclave”. Granted it is a sophisticated attack, but nevertheless one you’d want to prevent if only because it’s good practice to maintain a secure chain in which the individual links can trust each other.
For similar reasons the lockdown mode exists, which is mainly useful in limited scenarios (e.g. journalists, dissidents, etc).
On the other hand, if ever there was a potential attacker, it would be a government because they unlimited funds in theory and it isn’t hard to imagine the FBI trying to utilize this in the San Bernardino case if it was available.
A different risk, which would make the above quite a bit easier to accomplish, would be an altered biometrics scanner that, in addition to working the way it’s supposed to work, stores and sends off your biometrics or simply facilitates a replay attack.


Lossless is understood to have a bitrate of at least 1411kbps, or about 1.4Mbps.
Theoretical sustained bandwidth capability of Bluetooth on the 2.4Ghz spectrum is 1Mbps, but in practice it’s a chunk lower in part due to overhead.
Even if we assume if you could just cram a higher bitrate through a smaller bandwidth (spoiler, you can’t), everyone would be up in arms about Apple lying about lossless and class action suits would ensue.
That said, you can’t. This is not like your internet connection where you’ll just be buffering for a minute.
As for what is and isn’t perceptible, I think you’re mixing up your tonal frequencies with your bitrates here.


Honestly the most frustrating part is that there is plenty to criticize Apple on, so there’s no reason to get caught up in fabricated clickbaity nonsense.
But instead of focusing on genuine concerns, people would rather hop on some misinformation train.
All the while, if you espouse opinions that are bit more nuanced than “Apple bad”, then you must be a bootlicker like you said.
It’s as if people are more concerned about missing out on joining the hype and showing off their armchair skills, rather than exercising a modicum of critical thinking.


Obfuscating what you have to do ≠ not providing you with a roadmap on what you have to do.
If they didn’t obfuscate it there would be many tools out there already to let it be done.
This is a non sequitur.
It doesn’t automatically follow that a lack of tools means there is obfuscation. The simple fact that there can be many reasons why tools aren’t widely available alone breaks that logic.
But I’d say the fact that we already know exactly why difficulties arise when replacing parts, definitely proves that there’s no obfuscation.
Which again circles back to the difference between anti-repair and not pro-repair.
Just because Apple doesn’t go out of their way to provide a roadmap and hold your hand and as a result you are having difficulties when you’re trying to do it yourself, doesn’t mean they are actively thwarting you.
Apple doesn’t even think about you and me, their concern is to facilitate their own repair processes.
They literally serial lock almost half of their parts.
They don’t.
Aside from biometrics none of the parts are serial locked.
What you’re thinking about is parts based factory calibrated data loaded into the parts from a central database.
Just because the system ignores the calibration data once the part doesn’t match the one the calibration was intended for, doesn’t mean it’s “locked”, it just means that you’re trying to use calibration data for the wrong part.


Dude has reverse engineered pretty much the entire hardware stack of Macs to be able to provide the global community with Asahi, but because he says something you disagree with he’s supposedly “uninformed”.
Talk about childish…


I’m not sure if you’re serious or trying to be sarcastic.
Bluetooth and WiFi are two different things.
For starters standard Bluetooth operates on 1MHz wide channels, BLE on 2MHz wide channels, whereas WiFi (nowadays) operates on 20 or 40 MHz wide channels.
Modern Bluetooth (on 2.4Ghz) can theoretically do bursts of 2Mbps, but in practice even 1Mbps is hard to hit in a sustained fashion.
2.4Ghz is just a frequency band and is not the same as bandwidth.
You might as well argue that a pickup truck and a formula 1 race car should be able to reach the same top speed in the same time because their wheel distance is the same.
I think […]
Think again


Good for them, but this whole clickbait nonsense about Apple “locking” things is just that, nonsense.
Hector Martin, creator of Asahi Linux said it best so instead of repeating his words I’ll just leave a link to his comments on the matter: https://social.treehouse.systems/@marcan/110803356645502548
Oh wow, they really closed it down huh?
Not too long ago you were able to change it.
This dumbing things down to prevent customers from fucking themselves over and using up CS resources is getting ridiculous.
Say you need to change some settings but your modem/router isn’t online then you’re SOOL.
Cox, who uses the same gateway, is even worse. They won’t even allow you to enable legacy mode (802.11b) for IoT devices that cheaped out on WiFi cards, not even on a separate network and their customer service can’t enable it either.
I dread moving into a Cox region where there’s no fiber competitor available.
Only if there’s a risk at incriminating yourself, and if it’s not immediately apparent how you’d run that risk (e.g. you’re a witness that doesn’t have a direct relation to the crime at hand) you’d have to motivate how it could be incriminating.


You don’t know Some Software Corp and their world famous website somesoftwarecorp.com?


The proposal is bad enough as it is, but it’s the duplicitous gaslighting BS that really pisses people off.
If they came out and said “We came up with this thing to prevent loss of revenue on ads and prevent LLMs from capturing data” then people would still be against it, but at least it would feel like an honest discussion.
Instead it’s just another page out of Google’s playbook we’ve seen many times already.
For what it’s worth I blame W3C as well.
Their relatively young “Anti-Fraud Community Group” has essentially green lit this thing during meetings as can be seen here:
https://github.com/antifraudcg/meetings/blob/main/2023/05-26.md
https://github.com/antifraudcg/meetings/blob/main/2023/07-07-wei-side-meeting.md


WEI can potentially be used to impose restrictions on unlawful activities on the internet, such as downloading YouTube videos and other content, ad blocking, web scraping, etc.
Did the author of the article come from some dystopian parallel universe?


Well that explains why they did a 180 on their “no AI” rule, which has the mods in a tizzy.
Who knows, maybe it’ll cut back on the toxicity in the sense that you don’t have to interact with toxic people ¯\_(ツ)_/¯


But for iOS you’re forced to use Xcode for implementing certain things like permissions, build and upload.
You can do all that via VSCode as well if you so desire.
Permissions, configurations, etc. are essentially all just XML files and can be edited as such, building, running in simulator and uploading can all be done via CLI.
And if you’re not comfortable doing it via the terminal in VSCode, you can also find some extensions.
Personally as a native dev I don’t know why you’d want to of course, but to each their own.


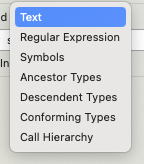
I think you might be misunderstanding what this does.
You did a search for symbol references that contain “User” ignoring cases.
When you do a search for symbol references this way, Xcode will return two things:
And it did just that.
The first three .swift files show references to symbols that contain “User”.
The forth one, User.swift, is in and of itself a symbol that matches the query and has symbols inside itself.
The last one UserViewModel.swift is in itself a symbol as well and all the parts that are nested within that you’ve annotated with underscores and question marks, serve to give you context about the symbol “UserViewModel”, hence the ellipses.
It’s essentially telling you “Hey I’ve found this symbol UserViewModel, it starts with a var named username, has a bunch of stuff following that (i.e. …) then has an extension, then some more stuff (i.e. …) and then ends”.
Without knowing what’s inside UserViewModel.swift I can’t tell if it goofed with giving you a typical declaration, but that doesn’t change the fact that its trying to give you context about a valid search result, the symbol UserViewModel, so that you can figure out if that’s the one you’re looking for.
Keep in mind that variables are considered symbols as well, but in this instance I don’t think that’s what happened here, otherwise it would’ve been marked with a P instead of a C.
If this is not desired behavior then I suggest you switch from “Containing” to “Matching Word” or instead consider using the search bar at the bottom of the Symbol Navigator.
Another option, if you’re searching while going through code, is to right click on the symbol in your code and click Find > Find Selected Symbol in Workspace.
Lastly it might be an idea to go over the Xcode documentation as a refresher. This would be a good starting point.
That said, Apple clearly feels that things can be improved by clarifying, because in the current Xcode beta they’ve changed the option label from References to Symbols (and added a few more options).


The presumption of innocence doesn’t preclude the fact that criminal courts don’t find someone innocent, rather they find someone not guilty.
This is for the simple fact that it’s neigh impossible to establish someone’s innocence, whereas it’s easier to establish that there isn’t enough evidence to consider someone guilty.
This case is, and sexual assault cases in general are, a great example why we can’t expect criminal courts to establish innocence.
These are often cases with little evidence available either which way, because often there are no other witnesses. Even if there would be physical evidence of a sexual act, it’s still challenging to prove under what circumstances those acts have occurred, specifically on the matter of consent.
To expect a court to be able to say with certainty that something hasn’t occurred is unreasonable.
That is not to say that it isn’t good that we have these high standards before we impose punishment onto someone, but it is important to recognize what it means when a court comes to a decision.
Additionally the presumption of innocence is just that, a presumption to establish who has the onus to prove something, there is no additional meaning attributed to it in the legal principle beyond establishing who has the onus to prove the facts at hand.
In that regard it’s rather unfortunately named, as it would’ve been more apt to name it “the presumption of not guilty” but I suppose that doesn’t roll as nicely off the tongue
To add to that, that the presumption is specifically a principle that only has meaning in criminal court, because the burden of proof is generally higher than in civil court.
People can be, and have been, found liable in civil court for the very thing a criminal court has found them “not guilty” on, on the very basis that criminal court can’t establish innocence and that the bar that needs to be met in civil court is generally lower than in criminal court.
As such to bring up the presumption of innocence in a vacuum is kind of like bringing up the generally recognized human right of freedom of speech when a social media company bans someone and removes their post.
Yes, the concept exists, but it’s irrelevant because it doesn’t apply to the topic at hand, because the concept aims to govern a very specific circumstance that isn’t applicable here and withholding the important context surrounding it (i.e. the role it plays in criminal court for the presumption and the fact that it only limits governments for the freedom of speech) masks the limitations of said concept.
None of the above aims to reflect my opinion on Spacey’s innocence (or lack thereof), rather it aims to provide the necessary details to put things into context.


Most of these services are US-centric because a lot of the necessary records to provide the information isn’t public in many countries outside of the US.
Birth records, death records, marriage records, divorce records, voting records, criminal records, etc. is considered public information in much of the US. Even address information can be found publicly and immigration records become available to the public after a certain time.
In a lot of countries, especially in many European countries, these are hard to access for people that aren’t the subject of these records, if accessible at all.
For example while court records are public in much of Europe, often times the names of private persons are censored because it’s not deemed necessary to know who the parties are to be able to check if the courts make fair decisions.
This automatically excludes criminal and divorce information from disseminating into the public.
Some countries will make some records public once the subject of those records have passed for X amount of years, but that’s still pretty rare.
As such services like these have limited use outside the United States.
Like some have pointed out there are ways to circumvent this, but it doesn’t make for a great experience, might cause issues down the line in particular with updates and there’s no guarantee it’ll keep working.
If you’ve purchased this form your company’s surplus and they refuse to unenroll from MDM I’d just give it back and ask for my money back, it’s not worth the hassle and the warranty is a nonsense reason since they can take the MBP off of their warranty service plan.
USPS’ website does this, sort of.
If their text service is down it’ll let you know and just skip the 2FA process even though normally they offer an option to get the code via email.
The fact that they do this is bad enough, the fact that this happens so often that I’ve seen this at least a dozen times is even worse.